In this post I disclosed what I mistakenly did.
This is very shocking event for me..
Then I fixed some countermeasures to avoid this kind of dangerous operations.
Red screen during user root
This makes red screen when you switch to root.
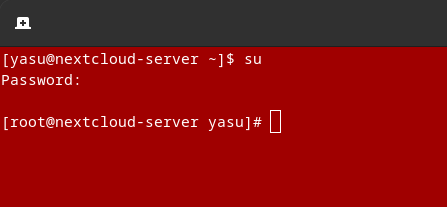
This is not valid during normal user.
This is video.
You can see red screen only when root user, right?
This is realized by /etc/bash.bashrc.
You can change the color “1B2224” to what you like.
if [ -n "$SSH_TTY" ]; then if [ $UID -eq 0 ]; then echo -e "\033]11;#A00000\a" else echo -e "\033]11;#1B2224\a" fi fi
This code enables to return normal configuration when you exit from root.
mysu() {
if [ 0 -eq $# ];
then
\su;. /etc/bash.bashrc
else
\su "$*";. /etc/bash.bashrc
fi
}
alias su='mysu'
Disallow sudo -s
Everyone likes “sudo -s” because it is convenient, right?
But it includes risks to run danger operations.
So I prevent this.
mysudo() {
if [ 0 -eq $# ];
then
\sudo
else
if [ "-s" == $1 ];
then
echo "This option is not allowed."
else
\sudo $@
fi
fi
}
alias sudo='mysudo'
Disallow rm by root
Adding rm to “not allowed list” in sudo configuration is also good.
$ sudo rm -rf / [sudo] password for yasu: Sorry, user yasu is not allowed to execute '/usr/sbin/rm -rf /' as root on nextcloud-server.
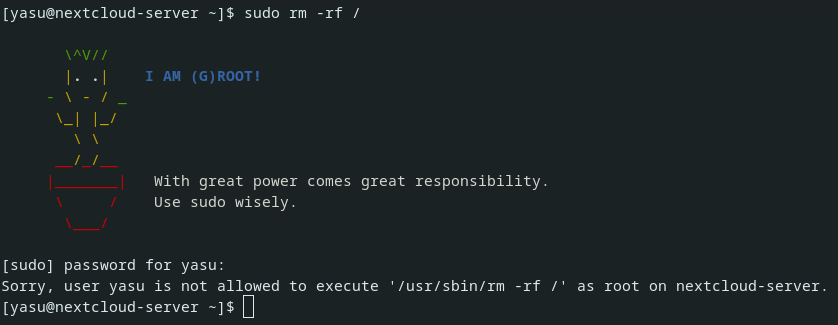
This can be realized by /etc/sudoers like this.
yasu ALL=(ALL:ALL) ALL, !/usr/bin/rm
Justify the location which can be run by sudo
Maybe this isn’t essential but I did it which limits the location of executable files which can be run from sudo.
Below configuration is deactivated so I activated.
Defaults secure_path="/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin"
Warning when you run sudo
As you can see below, I configured to show noticable image when running sudo to warn.

I completely referred this web site.
– Link
Changing editor for visudo
I changed editor configuration for visudo to vim on /etc/sudoers beacuse vi is too powerless…
Defaults editor=/usr/bin/vim
Conclusion
How was it?
If you have more idea, please message me!
Thank you!

Comments