I received this email after installing Rootkit Hunter.
I concluded they are not malicious files but detected by Rootkit Hunter.
– False positive.
I setup script which performs scanning by Rootkit Hunter everyday.
But I want to avoid unintentionally detecting then I configured white list.
In this article I will share it.
If you are interested in Rootkit Hunter and to be planned to install, this article is useful.
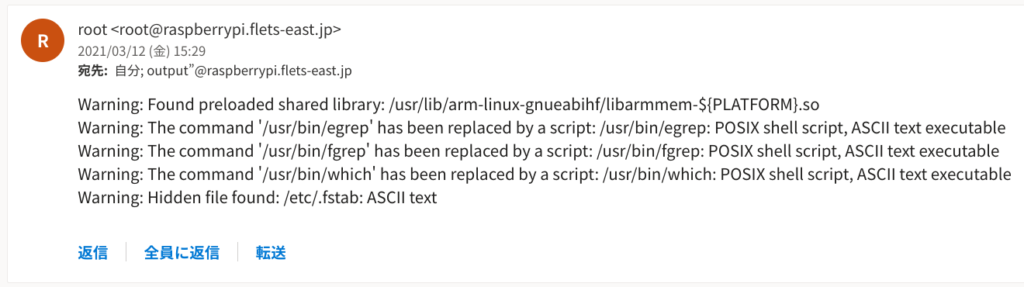
Found preloaded shared library:
These lines are useful to avoid it.
sudo vim /etc/rkhunter.conf
# Adding this line to rkhunter.conf
SHARED_LIB_WHITELIST=/usr/lib/arm-linux-gnueabihf/libarmmem-${PLATFORM}.so
Firstly I assumed
${PLATFORM} is environment variables and should be replaced by actual file name.
Then I configured as below but didn’t make sense.
# To find actual file name ls -l /usr/lib/arm-linux-gnueabihf/libarmmem-*.so lrwxrwxrwx 1 root root 16 Apr 30 2019 /usr/lib/arm-linux-gnueabihf/libarmmem-aarch64.so -> libarmmem-v7l.so -rw-r--r-- 1 root root 9512 Apr 30 2019 /usr/lib/arm-linux-gnueabihf/libarmmem-v6l.so -rw-r--r-- 1 root root 17708 Apr 30 2019 /usr/lib/arm-linux-gnueabihf/libarmmem-v7l.so lrwxrwxrwx 1 root root 16 Apr 30 2019 /usr/lib/arm-linux-gnueabihf/libarmmem-v8l.so -> libarmmem-v7l.so # Configuring them to rkhunter.conf SHARED_LIB_WHITELIST=/usr/lib/arm-linux-gnueabihf/libarmmem-aarch64.so SHARED_LIB_WHITELIST=/usr/lib/arm-linux-gnueabihf/libarmmem-v6l.so SHARED_LIB_WHITELIST=/usr/lib/arm-linux-gnueabihf/libarmmem-v7l.so SHARED_LIB_WHITELIST=/usr/lib/arm-linux-gnueabihf/libarmmem-v8l.so
I setup without replacing ${PLATFORM}, then warning was removed.
The command … has been replaced by a script:
I configured like this.
sudo nvim /etc/rkhunter.conf # Configuring rkhunter.conf SCRIPTWHITELIST=/usr/bin/egrep SCRIPTWHITELIST=/usr/bin/fgrep SCRIPTWHITELIST=/usr/bin/which
According to original warning message, egrep/fgrep/which are script.
So I checked if they are really OK, and they are.
cat /usr/bin/egrep
#!/bin/sh
exec grep -E "$@"
cat /usr/bin/fgrep
#!/bin/sh
exec grep -F "$@"
cat /usr/bin/which
#! /bin/sh
set -ef
if test -n "$KSH_VERSION"; then
puts() {
print -r -- "$*"
}
else
puts() {
printf '%s\n' "$*"
}
fi
(snip)
Hidden file found:
According to warning message, “/etc/.fstab is hidden file”.
I checked the contents of this.
cat /etc/.fstab proc /proc proc defaults 0 0 PARTUUID=0d91114b-01 /boot vfat defaults 0 2 PARTUUID=0d91114b-02 / ext4 defaults,noatime 0 1
It looks OK then I added to white list as well.
sudo nvim /etc/rkhunter.conf # Adding this line to rkhunter.conf ALLOWHIDDENFILE=/etc/.fstab
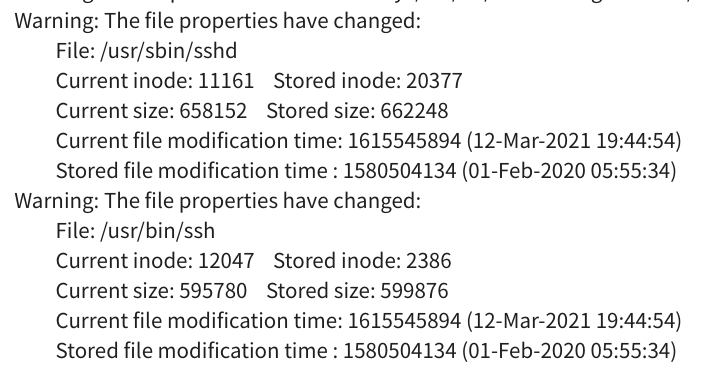
sshd and other files are detected
I thought “It is OK…” but it is not.
After a few days sshd/ssh are detected.
I am trying to solve them.
Conclusion
How was it?
I think receiving email regarding ssh/sshd is annoying, I am working on it!



Comments